- Topic1/3
18k Popularity
37k Popularity
20k Popularity
6k Popularity
173k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is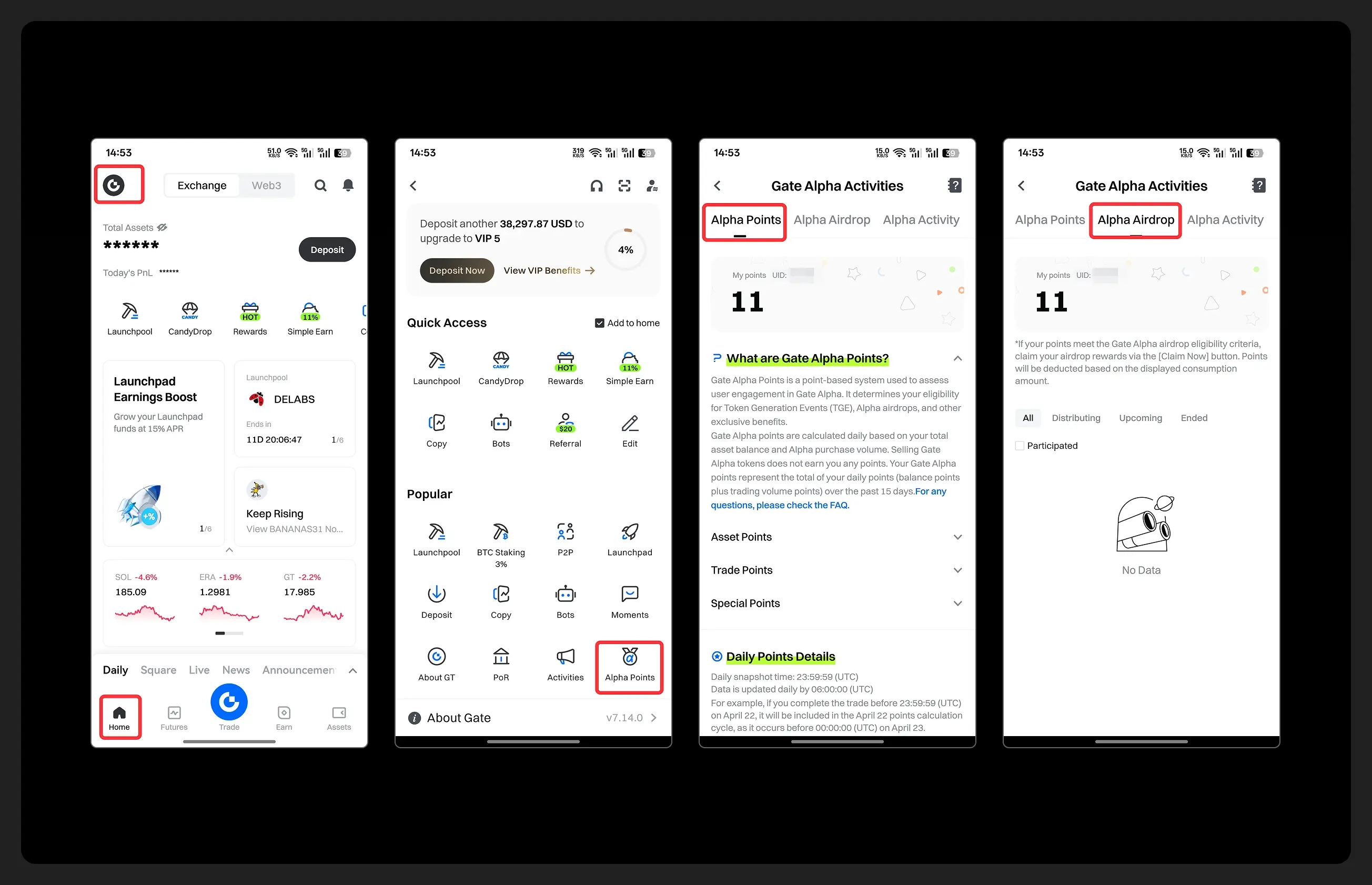
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
Ika Network introduces sub-second level MPC infrastructure to empower the Sui ecosystem.
Ika Network: Sub-second MPC Infrastructure
The newly launched Ika network of the Sui ecosystem is an innovative infrastructure based on multiparty secure computation (MPC) technology, with the main feature being sub-second response speed. Ika is highly compatible with Sui in terms of underlying design such as parallel processing and decentralized architecture, and will be directly integrated into the Sui development ecosystem in the future, providing plug-and-play cross-chain security modules for Move smart contracts.
The core technology of Ika includes:
Improved 2PC-MPC signature protocol, which decomposes the signing operation into a process involving both the user and the network.
Utilize parallel computing to split the signature task into multiple subtasks for simultaneous execution, significantly improving speed.
A large-scale network supporting thousands of nodes, each node only holds a part of the key shard.
Cross-chain control and chain abstraction, allowing smart contracts on other chains to directly control accounts in the Ika network.
Ika is expected to have the following impacts on the Sui ecosystem:
Provide cross-chain interoperability, supporting the low-latency and high-security integration of assets such as BTC and ETH into the Sui network.
Provide a decentralized asset custody mechanism, which is more flexible and secure than traditional centralized custody.
Simplify cross-chain interaction processes, allowing contracts on Sui to directly operate accounts and assets on other chains.
Provide a multi-party verification mechanism for AI automation applications to enhance transaction security and credibility.
However, Ika also faces some challenges:
As a "universal standard" for cross-chain interoperability, it needs to gain more recognition from blockchain and projects.
The issue of the irreversibility of MPC signature permissions remains to be resolved.
Dependence on the stability of the Sui network, and adjustments may be needed in line with Sui consensus upgrades.
Comparison of Privacy Computing Technologies
FHE Project
Zama & Concrete:
Fhenix:
TEE Project
Oasis Network:
ZKP Project
Aztec:
MPC Project
Partisia Blockchain:
Comparison of Privacy Computing Technologies
Overview of Different Technologies
Fully Homomorphic Encryption ( FHE ):
Trusted Execution Environment ( TEE ):
Multi-Party Computation ( MPC ):
Zero-Knowledge Proof ( ZKP ):
Technical Adaptation Scenarios
Cross-chain signature:
DeFi Multi-signature Wallet/Custody:
AI and Data Privacy:
Technical Differentiation
Performance and Latency: FHE > ZKP > MPC > TEE( from high to low )
Trust assumption: FHE/ZKP > MPC > TEE( from weak to strong)
Scalability: ZKP/MPC > FHE/TEE
Integration Difficulty: TEE < MPC < ZKP/FHE
FHE is not universally superior to other solutions
FHE, TEE, ZKP, and MPC face the "impossible triangle of performance, cost, and security" in practical applications. FHE theoretically provides the strongest privacy protection, but its low performance limits its applications. TEE, MPC, and ZKP are more feasible in scenarios that are sensitive to real-time requirements and costs.
Different technologies have different trust models and applicable scenarios:
Future privacy computing may be a complement and integration of various technologies, such as Nillion combining MPC, FHE, TEE, and ZKP. The choice of appropriate technology should depend on specific needs and performance trade-offs, in order to build a modular solution.